QuSecure Honored as Global Product Leader in Post-Quantum Cryptography by Frost and Sullivan
“Trust in digital systems is a vulnerability… It’s the most dangerous vulnerability in the world because its the only [vulnerability] thats also an exploit at the same time.”
John Kindervag, Father of Zero Trust
As organizations face increasingly sophisticated cyber threats and the growing complexity of networks and data access, the traditional perimeter-based security model has proven to be insufficient.
Zero Trust has emerged as a popular security strategy aiming to reduce vulnerabilities within a network by assuming no implicit trust and instead requires verification for every user and device attempting to access resources. Its focus on continuous authentication, strict access controls, and least privilege aligns with the need for enhanced security in an increasingly interconnected and digital world.
Fundamentally, a zero trust architecture (ZTA) is the application of the principle “never trust, always verify” to network security. ZTA dictates specific design and deployment of security measures, policies, and technologies to achieve the goals of zero trust and further secure assets within a network.
We can illustrate the differences between perimeter-based security and a zero trust architecture by way of an analogy. Consider an office building with a single locked front door. In perimeter-based security, security resources are focused on fortifying the security of the door entrance, perhaps with locks, cameras, and a door made from sturdy material. Once you have passed the door, you are considered trusted and can freely move about the office building and examine its contents (ie. its many floors, office spaces, and rooms). Security comes down to a single check point: the front door.

By way of contrast, consider the same scenario with zero trust architecture applied. The office building is secured with the same front door, fortified with locks, cameras, etc. with the addition of a key card. The key card system verifies your identity and you use your standard key to unlock the door. Upon entering into the building and passing through the entryway to your office’s door you are met with another key card swipe sensor which you use to verify your identity. Once in the office you arrive at your division’s section door where you must repeat the process of verifying your identity and entering a 4 digit code before entering. When arrived in your section of the office at every door you must repeat this identity verification process. Notably, at several doors you are able to verify yourself with the key card, but the door does not open for you – you do not have access to those rooms.
With ZTA, at each doorway within the house, your identity is established and your permissions are verified before proceeding. At no point in your journey is trust assumed by virtue of your being in the building. Rather, it is continually earned.
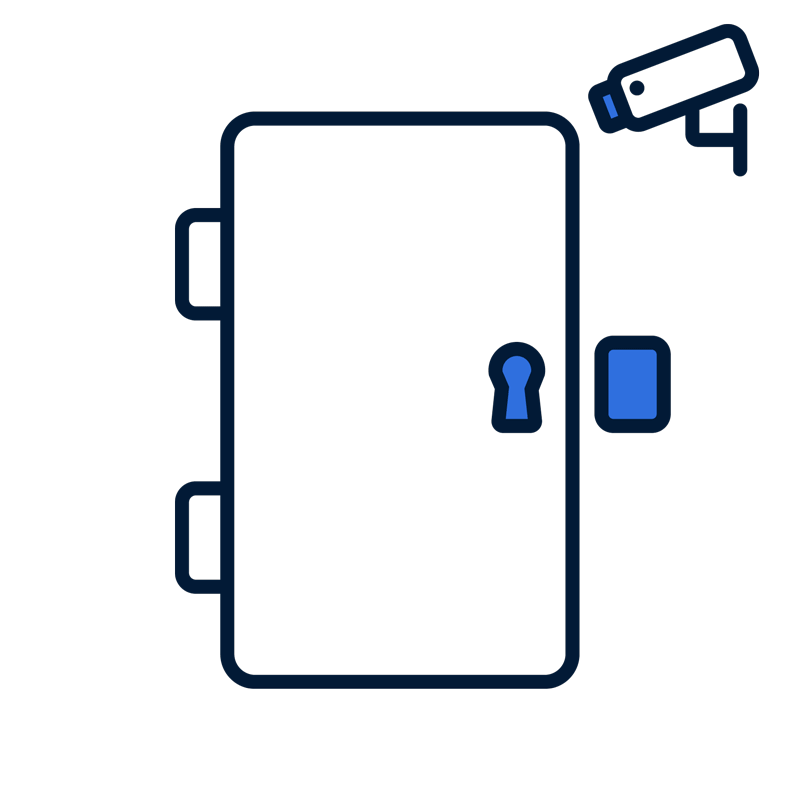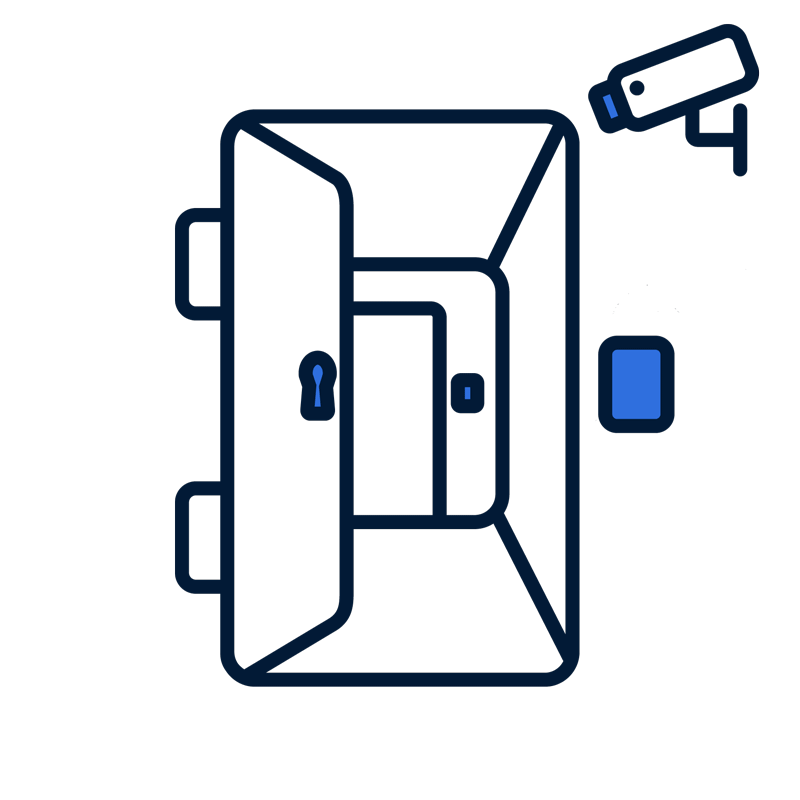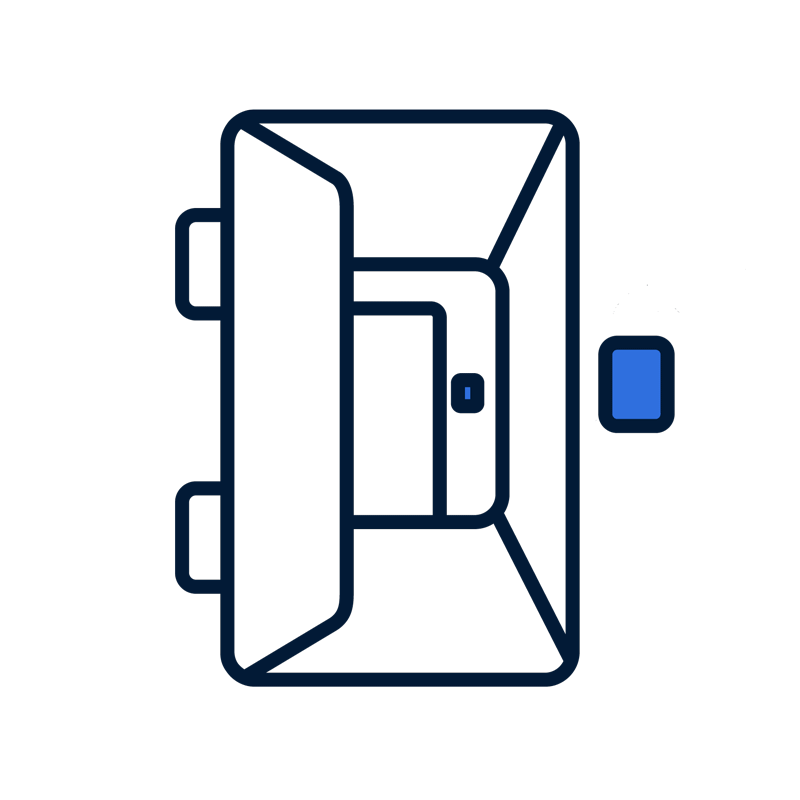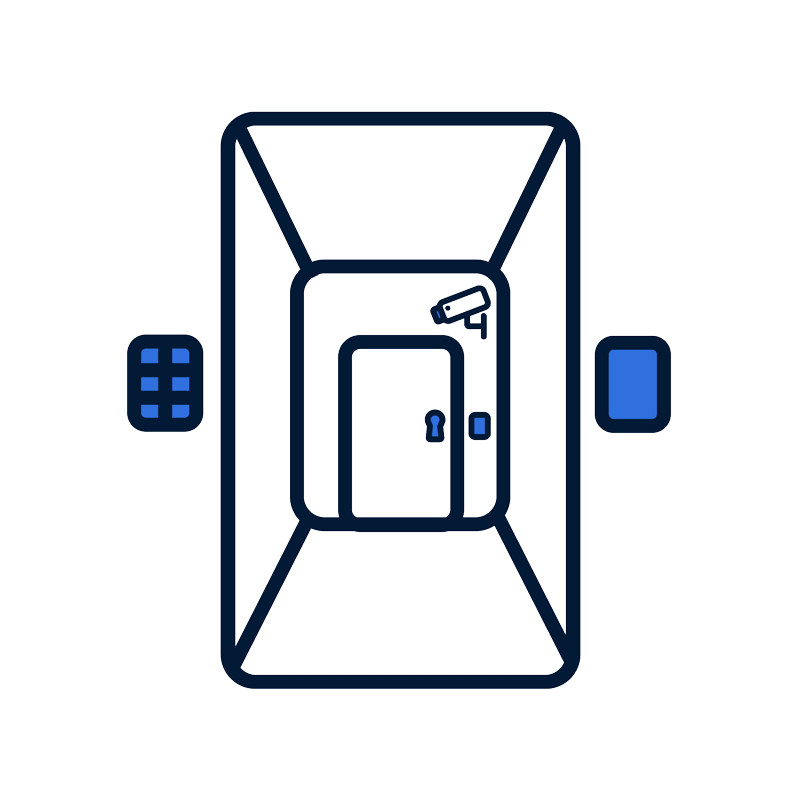
In reality networks are not typically as simple as an office building with a single door, they are much more complex. For organizations that manage complex networks that include tens, hundreds, or thousands of heterogeneous services, remote workers, bring-your-own-device (BYOD), etc. perimeter-based security simply leaves too much space open for exploit compared to ZTA.
“Input and cooperation from various stakeholders in an enterprise is needed for a zero trust architecture to succeed in improving the enterprise security posture.”
NIST
By adopting zero trust architecture standards, businesses enhance their overall cybersecurity – shifting from a perimeter-based security model to more robust frequent check point style model. ZTA helps business leaders reduce the risk of data breaches, unauthorized access, and lateral movement within their networks, ultimately safeguarding their assets and maintaining the trust of their customers.
QuProtect is architected to support a zero trust strategy for organizations across the public and private sectors. Our service mesh architecture brings the key zero trust principles of authentication and authorization to life for secure network communication.
Simply put, the process of authentication aims to answer the question of, “Who are you?”. QuProtect’s architecture and processes support this key principle and ensuring resources (ie. device, data source, and computing services) are who they say they are.
Proving Who’s Who By Defining Resources
Under a Zero Trust Architecture model, when any resource in a network seeks to connect and communicate with another resource, both resources must first demonstrate valid identity.

Introducing Quark
QuSecure’s quantum orchestrator, Quark, is the backbone to QuSecure’s QuProtectTM post-quantum solution. As a central, post-quantum secure hub, Quark “orchestrates” device enrollment and authentication of PQC (Post Quantum Cryptography) sessions.
When you start using QuProtect, all resources must be registered by an appropriately permissioned and authenticated human with Quark via the QuProtect administrative dashboard. This registration process ensures that resources that connect within a network are clearly and purposefully identified.
Once a resources identity is known via the authentication process, the question of “Do you have permission to access a particular resource?” must be answered. The process of answering this question is known as Authorization.
Permission To Communicate Via Policy
Under a Zero Trust Architecture model, once a device demonstrates its identity, before it can communicate with another defined device, permission must be established.
After registration, Quark grants permissions for communication between devices via administrative defined policies. If permission is in place devices can connect with each other for communication.
Within the QuProtect control plane, there are two important functions that are responsible for granting access to resources and for establishing communication channels between resources (note that these paths are not the communication connections themselves). These two functions are housed in what is referred to as the “Policy Decision Point” by NIST.
While the Policy Decision Point (PDP) makes the rules about if connections can happen, it does not actually make them happen. That functionality belongs to the “Policy Enforcement Point.”
The Policy Enforcement Point (PEP) is the part of Quark’s functionality that makes connections on the channels laid by the PDP. Connections are also monitored and ultimately terminated by the PEP.
Trust Does Not Last, It Requires Constant Renewal
Under a Zero Trust Architecture model, devices are not to be trusted beyond the duration of a single transaction.
When devices are granted permission to communicate via Quark those permissions expire after a set amount of time. To reconnect devices must once again request connection permission from Quark.
Record of Activities
It comes as no surprise that with this level of increased security and constant activity to ensure resources and their connections are verified, that a thorough record of all occurrences must be kept.
Quark’s logs house details of all happenings within the service mesh. With access to logs the full record is easily auditable.
Observability For Actionable Insights
The authentication and authorization processes of zero trust architecture introduce new additional enforcement points. Each of these stops in tandem with the logged activities enable the opportunity for observability and insights. This heightened observability enables better security policy decisions to be made.
Schedule a demo of QuProtect and see how you can strengthen your organization’s security posture and ensure the trust and confidence of your customers. Start the journey towards zero trust today and safeguard your business from evolving threats.